Demeter's Hymn to Cybersecurity: Consequences of Cyberattacks on Scale-Ups
How many entrepreneurs feel a filial connection with their business, such as Demeter’s passion for Persephone? If Hades abducted Persephone on his golden chariot drawn by immortal horses, the infants of start-up founders are threatened by a more nebulous danger: cyberattacks.

Cyberattacks: the Persephone's abduction of founders.
The ancient Greek Homeric Hymns narrate the myth of Demeter, goddess of harvests and growth (1). She becomes desperate when her precious daughter, Persephone, is abducted by Hades, the god of the dead. Starts a long journey for Demeter to find the identity of her daughter’s kidnapper and to obtain her return.
How many entrepreneurs feel a filial connection with their business, such as Demeter’s passion for Persephone? At least, it has been the case for one of the most successful of them, Elon Musk. Tesla and SpaceX's founder once stated that “creating a company is like raising a child” (2).
“Building a company is like having a child: you nurture it, take care of it even when it will ruin you.” Here you see the raw emotion of the toll @tesla @SpaceX took for @elonmusk to make it what it is today. Never give up. pic.twitter.com/abBHD4Ar5B
— Tesla Silicon Valley Club (@teslaownersSV) February 23, 2021
If Hades abducted Persephone on his golden chariot drawn by immortal horses, the infants of start-up founders are threatened by a more nebulous danger: cyberattacks.
This article provides some insight into the extent to which scale-ups are vulnerable to cyberattacks. In recent years, there has been a significant increase in the share of companies targeted that are scale-ups. Despite their limited size, the consequences of these attacks are especially pernicious for these businesses.
While looking for Persephone, Demeter stopped protecting farmers. The Earth was then on the verge of starvation. For their part, entrepreneurs battling cyberattacks can not foster their company’s growth anymore. Floating downstream the Styx, their business thus slowly disappears in the kingdom of promising but perished scale-ups.
Scale-ups: malicious hackers' new target.
Having analyzed 2,013 data breaches, Verizon’s 2019 Data Breach Investigations Report disclosed that "43% of breaches involved small business [less than 1,000 employees] victims" (3).
Two years later, their report underscored that the gap had considerably shrunk between the number of breaches in large and small organizations. The authors noted that "last year [2020], small organizations accounted for less than half the number of breaches that large organizations showed [...] this year these two are less far apart with 307 breaches in large and 263 breaches in small organizations" (4).
The report stresses that the nature of cyberattacks suffered by large and small businesses is converging as well. In both cases, the majority of incidents are carried out by external actors on credentials and personal data through system intrusions, miscellaneous errors, and basic web application attacks.
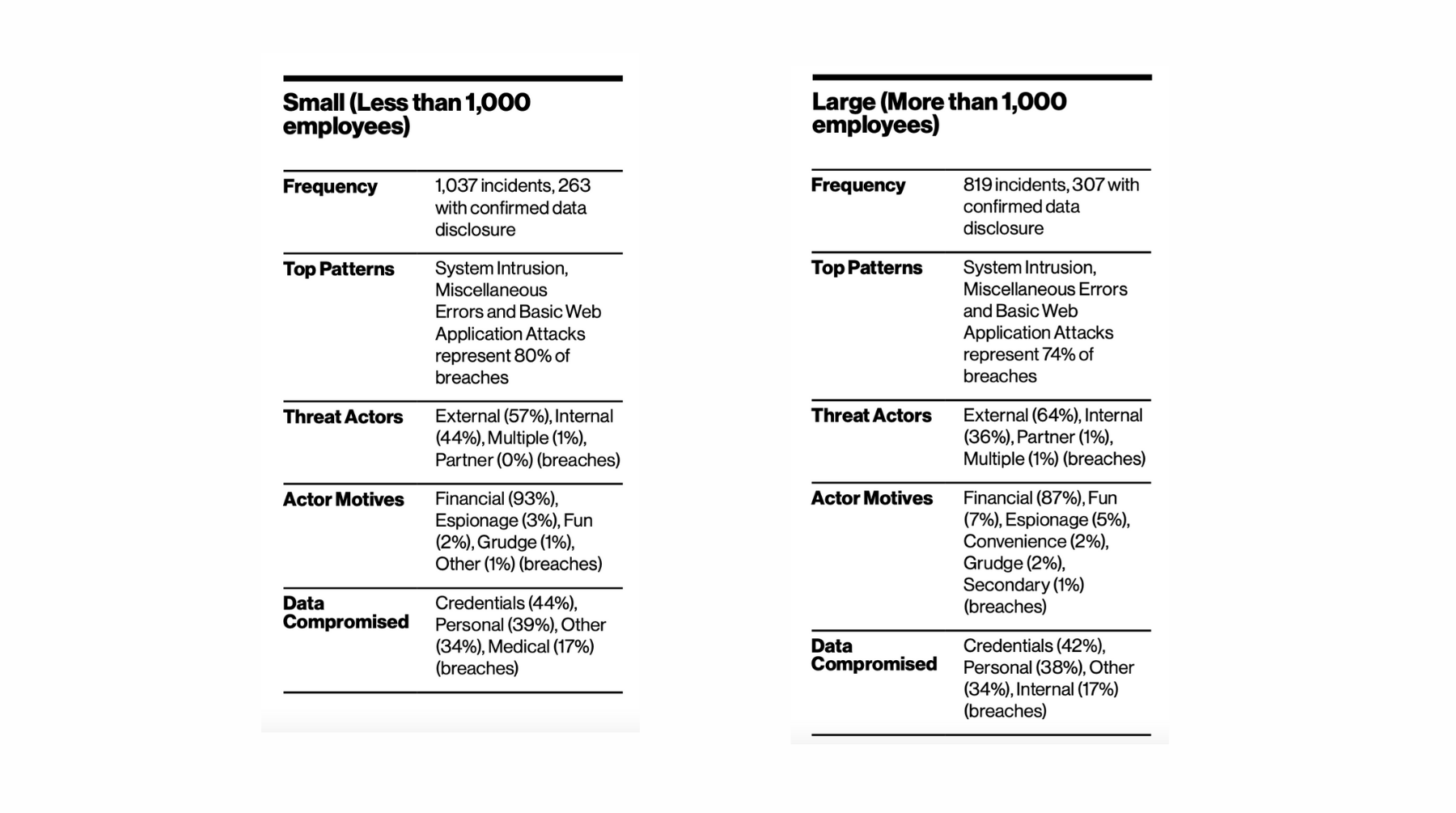
Beyond conjectural dynamics, such as the rise of remote working, scale-ups are inherently exposed to cyberattacks because of their limited resources. Microsoft 365 Team puts forward five major flaws within small businesses which prevent them from being resilient to cyberthreats (5):
- "they can't afford dedicated IT staff" ;
- "inadequate or non-existent computer and network security" ;
- "lack of a backup plan" ;
- "employees unknowingly help cybercriminals attack businesses" ;
- "small businesses are comparatively easy to attack".
Cost of cyberattacks: a serious increase for scale-ups.
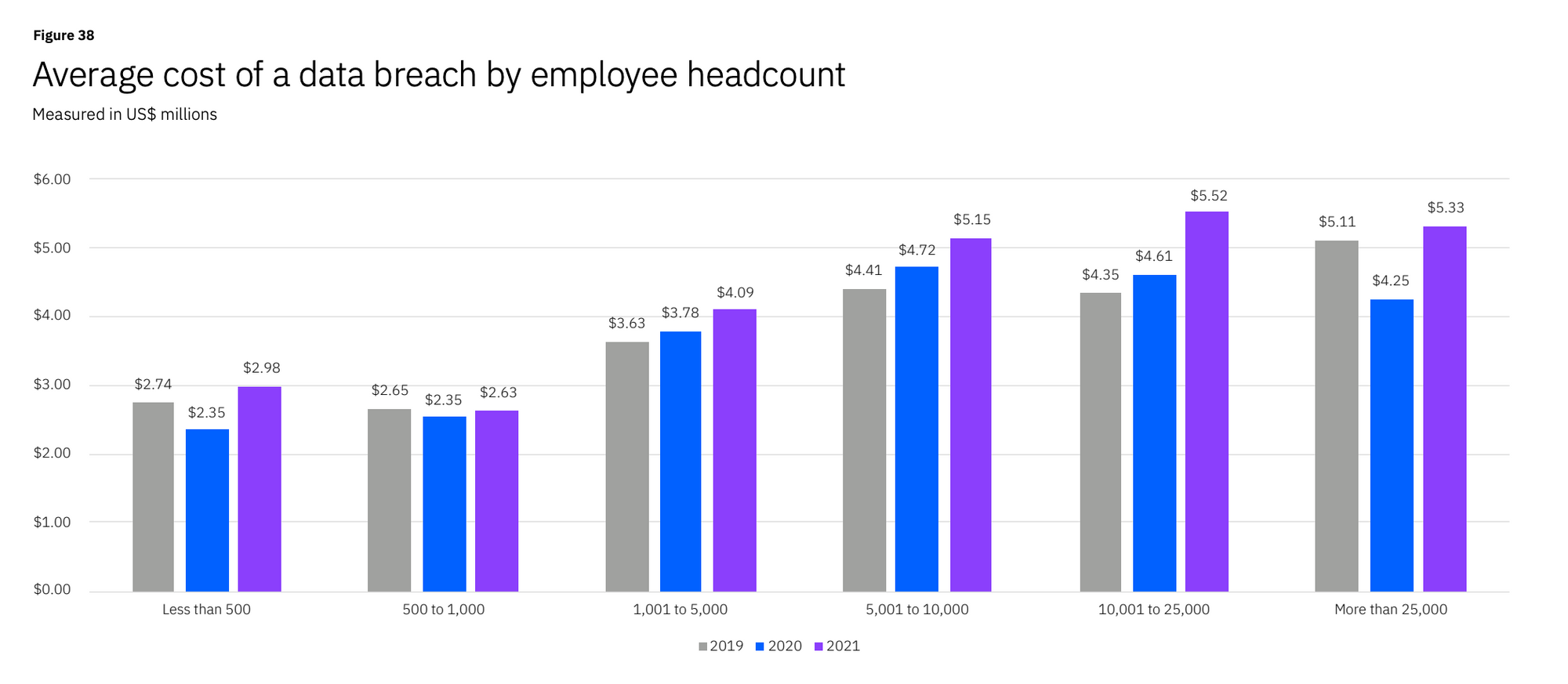
IBM’s 2021 Report revealed that the cost of data breaches for small businesses [less than 500 employees] increased by 26.8% in the past year: from 2.35 million in 2020 to $2.98 million in 2021" (6).
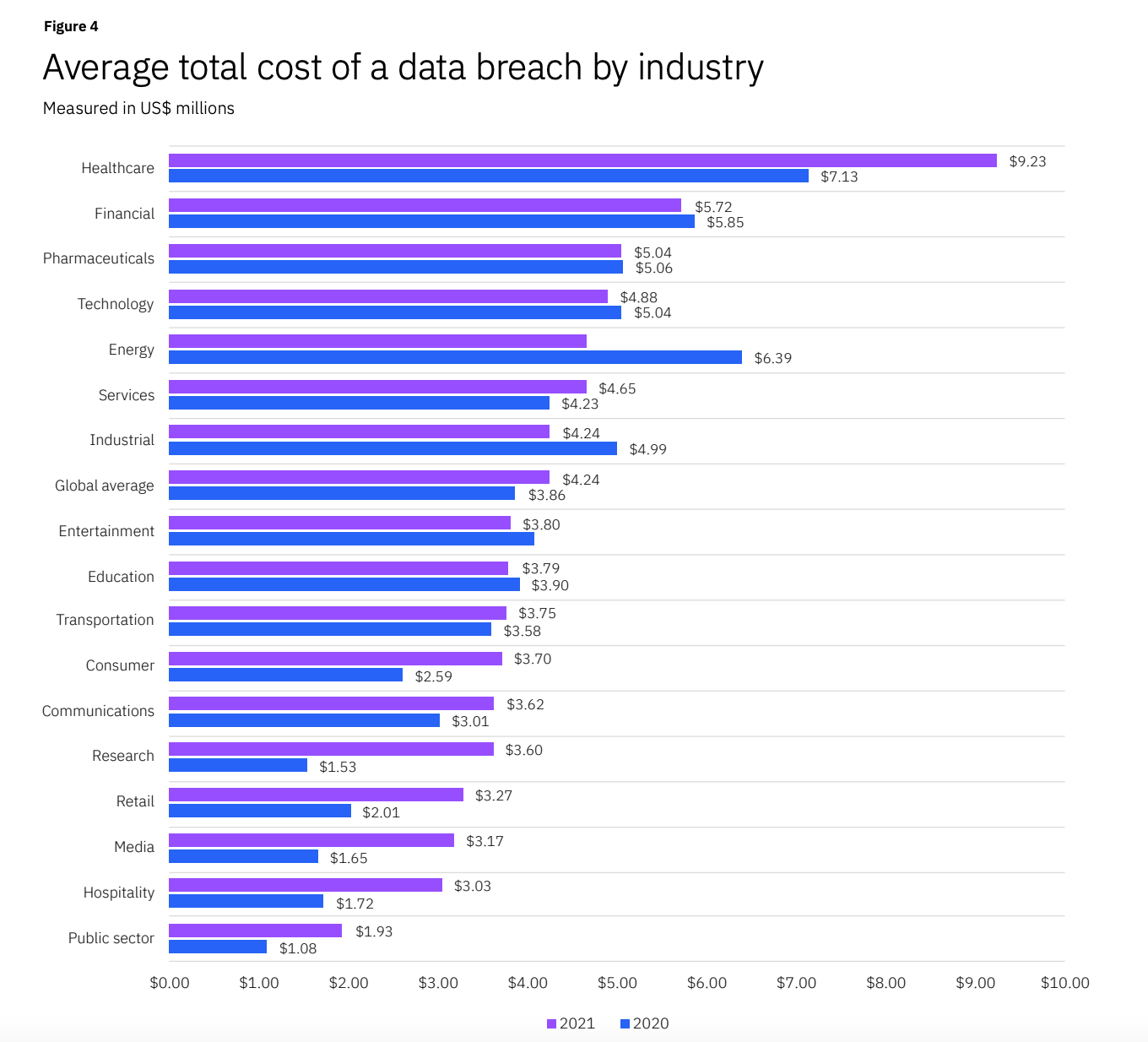
Furthermore, the report sheds light on the fact that healthcare and finance are the top industries in average data breach cost. It comes with no surprise that these two sectors, along with their "tech" suffixes, are among the most promising ones for start-ups.
According to KPMG, “global fintech investment continued its remarkable rebound in H1’21, rising from $87 billion in H2’20 to $98 billion in H1’21. Fintech deal volume hit a new record of 2,456 during H1’21” and “global VC investment reached over $52 billion in H1’21” (7).
The growth of data breach costs for FinTech implies that banking and financial companies will increasingly seek to ensure the cybersecurity of their digital transactions against cyberattacks and ransomware. Moreover, they already have to comply with international security norms, for instance, the PCI DSS requirements (8).
According to Dealroom, “2021 was a record year for global healthtech investment, with $62.5 billion raised” and “healthtech companies globally have reached a combined value of $1.7 trillion” (9). They also have to specifically protect their users' data in light of the HIPAA (The Health Insurance Portability and Accountability Act) in the United States or the HDS (Hébergement des données de santé) in France (10) (11).
Security by design: the key for Persephone's return.
Having learned from Helios, god of the sun, that her daughter was detained by Hades, Demeter required the intervention of Zeus, king of the gods, to settle their dispute. She finally obtained that Persephone would live eight months on Earth with her and the four others in the underworld with Hades. Hence, seasons were born.
Rare are the start-up founders who can benefit from such a divine mediation when their business is facing cyberattacks.
If public authorities are no god, they gradually grasp the importance of this matter. As soon as 2017, the United States Congress adopted the "NIST Small Business Cybersecurity Act" (12). This bill requires the National Institute of Standards and Technology (NIST), a federal agency, to provide small businesses with tools in order to mitigate the risk of cyberattacks.
In France, a recent report from the Senate (13) tackled the same issue. It recognized that the French National Agency for the Security of Information Systems (ANSSI) is fully involved in the protection of operators of vital importance. These companies are thus particularly resilient to cyber threats. However, the report highlights that the State's measures do not support small companies sufficiently in their struggle to enforce cybersecurity practices.
To fill this gap, the report calls for the development of tools to ensure "security by design". In other words, developers should include security in their to-do lists when they are building and improving their software.
Escape enables them to do just that. Our platform runs more than one thousand automated security checks on GraphQL APIs, directly inside their CI/CD pipeline. It detects more than forty kinds of vulnerabilities and provides developer-friendly advice on how to fix them.
Demeter had to get to the top of the Olympus to get Persephone back. Save yourself the trouble and escape with us.

Wanna know more about Security? Check out our blog post "9 GraphQL Security Best Practices" and learn how to build safe GraphQL APIs.
Bibliography
(1) Rayor, Diane J. et Diane J. Rayor. The Homeric hymns. Updated edition. Berkeley: University of California Press. 2014.
(2) [Tesla Silicon Valley Club].““Building a company is like having a child: you nurture it, take care of it even when it will ruin you.” Here you see the raw emotion of the toll @tesla@SpaceX took for @elonmusk to make it what it is today. Never give up.” Twitter, February 23, 2021, https://twitter.com/teslaownersSV/status/1364059868030668800?ref_src=twsrc^tfw|twcamp^tweetembed|twterm^1364059868030668800|twgr^|twcon^s1_&ref_url=https%3A%2F%2Fblog.escape.tech%2Fp%2F0a726781-3737-4092-a638-744a3314c1bf%2F.
(3) “2019 Data Breach Investigations Report.” Verizon, 2019, https://www.spambrella.com/wp-content/uploads/2020/05/Verizon-2019-Data-Breach-Investigations-Report.pdf.
(4) “2021 Data Breach Investigations Report.” Verizon, 2021, https://www.verizon.com/business/resources/reports/2021-data-breach-investigations-report.pdfx?mkt_tok=MTU3LUlQVy04NDYAAAGDc_A36GPK8kHJfWCkED4F9hpva1IK3CB3kUQJbtckI917m69G8ZqJc2pmcc6u4lWj3ed2j7LwLrsqDBoPi5btkOVMjqY1UydCFfEp1xuWQchbsBbc.
(5) Microsoft 365 Team. "What small businesses need to know about cybersecurity." Microsoft, October 14, 2019, https://www.microsoft.com/en-us/microsoft-365/business-insights-ideas/resources/cybersecurity-small-business.
(6) “Cost of a Data Breach Report 2021.” IBM Security, July 2021, https://www.ibm.com/downloads/cas/OJDVQGRY.
(7) “Pulse of Fintech H1’21.” KPMG, August 2021, https://assets.kpmg/content/dam/kpmg/xx/pdf/2021/08/pulse-of-fintech-h1.pdf.
(8) "Maintaining payment security." PCI Security Standards Council, https://www.pcisecuritystandards.org/pci_security/maintaining_payment_security.
(9) “2021, a breakthrough year for Healthtech & Biotech.” Dealroom, January 2022, https://dealroom.co/uploaded/2022/01/Dealroom-report-health-jan2022.pdf?x21552.
(10) "Health Insurance Portability and Accountability Act." Congress.gov, March 18th, 1996, https://www.congress.gov/bill/104th-congress/house-bill/3103.
(11) Article L1111-8 du Code de la santé publique. Légifrance, version en vigueur depuis le 01 avril 2018, https://www.legifrance.gouv.fr/codes/article_lc/LEGIARTI000033862549/.
(12) “NIST Small Business Cybersecurity Act.” Congress.gov, March 4th, 2017, https://www.congress.gov/bill/115th-congress/house-bill/2105.
(13) Meurant, Sébastien & Rémi Cardon. "La cybersécurité des entreprises - Prévenir et guérir : quels remèdes contre les cyber virus ?". Rapport d'information n° 678 (2020-2021) - Sénat, déposé le 10 juin 2021, http://www.senat.fr/rap/r20-678/r20-678.html.
(14) "The Return of Persephone." Met Museum, https://www.metmuseum.org/art/collection/search/847023.
